CloudStack: Firewall
Posted: Wed Jul 10, 2013 3:00 am
Hello !
As you probably found out, the default security group does not allow any connections from outside to your VM, IPv4 TCP/UDP/ICMP connections are totally blocked.
This is intended, if you wish to provide a specific service to the internet, you will need to open the port(s) for the service. It saves us from some types of attacks, such as DNS amplification DDoS when careless admins leave the dns open and in some cases even recursive, many times it is not even needed or used.
But I digress.
In order to open a specific port, you need to go to Network and select as view Security Groups:
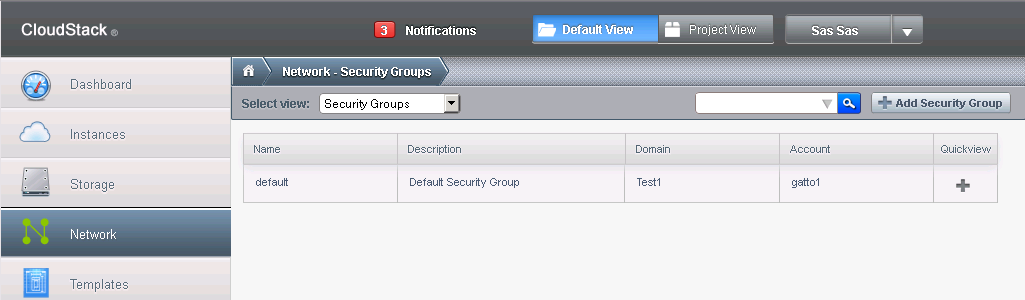
As you can see, there is the Default security group there already.
Let's look at what it does for incoming connections (click on default and selected "Ingress Rule" tab):
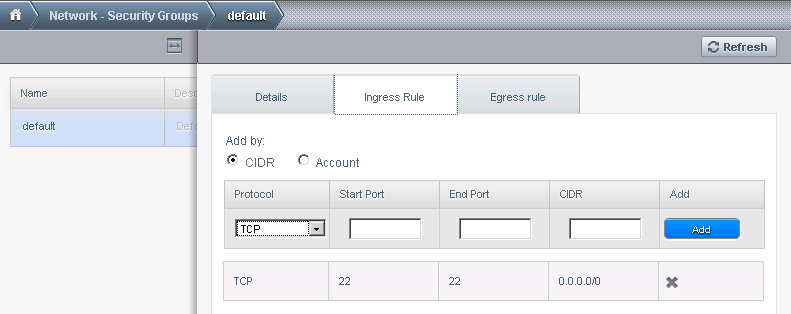
This allows access to port 22 TCP from all over the internet as uncle added the rule before, but is disabled by default, everything is blocked.
Let's add another rule, say, we wish to run a web server and want to allow HTTP and HTTPS traffic, that being TCP ports 80 and 443.
We will add the rules like this:
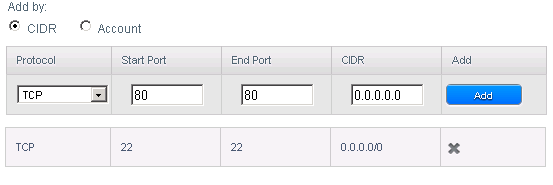
Click the add button and repeat with port 443 instead of 80.
The end result is this:
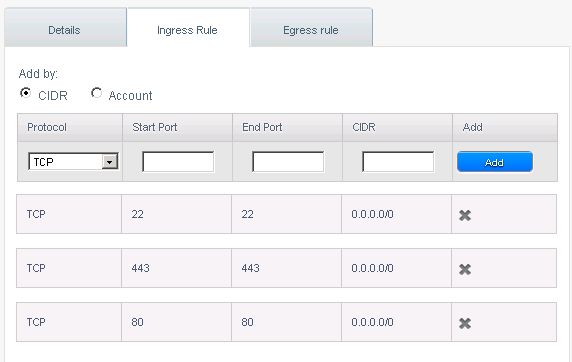
If you wish your changes to be valid for all VMs in the account, you can do this in the account view by selecting the account radio button.
The same applies to UDP and ICMP.
In order to allow all incoming traffic, just put the start port 1 and end port 65535 on TCP and UDP. ICMP is portless, therefore you need to add only the CIDR address to allow from the whole internet (0.0.0.0/0).
You can also fine tune this in order to allow only one IP, such as 123.123.123.123/32 presuming the ip is 123.123.123.123 or the whole class c, presuming you have IPs in that range (123.123.123.1-123.123.123.254 which translates to 123.123.123.0/24).
Example:
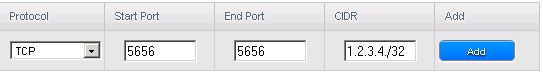
I am running a billing panel on a server some place and wish to allow it to access the solusvm master that i run on a VM in the cloud with Prometeus/Iperweb and deny access to everyone else. Let's suppose the IP where I run the billing panel is 1.2.3.4 and port for solusvm is 5656 (for SSL as it should be used by any sane host) So, I am adding the rule for TCP traffic, port starting at 5656 and ending at 5656 and as CIDR I add the billing panel IP which is 1.2.3.4 and the netmask for only one IP which is 32, so we have:
I strongly advise everyone not to open all ports by default unless they know how to stop all redundant services or not to installt hem at all. Our templates are minimalistic running only port 22 ssh, however, many applications install by default services which are not needed and this increases the risk for 0 days exploits, even if you keep them updated daily. Instead, consult your application documentation and open only the ports needed for it to function. If you know what you are doing, and I suppose most our customers do, go ahead :) Our regular VPSes have all ports open by default, this only eliminates the need for running a firewall in mostt cases, it is not put there to limit you in any way shape or form.
We may offer another security model with all ports open.
Note: IPv6 is still wide open, you will have to use the VMs firewall to filter IPv6 if you choose to enable it and need to offer services over IPv6.
As you probably found out, the default security group does not allow any connections from outside to your VM, IPv4 TCP/UDP/ICMP connections are totally blocked.
This is intended, if you wish to provide a specific service to the internet, you will need to open the port(s) for the service. It saves us from some types of attacks, such as DNS amplification DDoS when careless admins leave the dns open and in some cases even recursive, many times it is not even needed or used.
But I digress.
In order to open a specific port, you need to go to Network and select as view Security Groups:

As you can see, there is the Default security group there already.
Let's look at what it does for incoming connections (click on default and selected "Ingress Rule" tab):

This allows access to port 22 TCP from all over the internet as uncle added the rule before, but is disabled by default, everything is blocked.
Let's add another rule, say, we wish to run a web server and want to allow HTTP and HTTPS traffic, that being TCP ports 80 and 443.
We will add the rules like this:

Click the add button and repeat with port 443 instead of 80.
The end result is this:

If you wish your changes to be valid for all VMs in the account, you can do this in the account view by selecting the account radio button.
The same applies to UDP and ICMP.
In order to allow all incoming traffic, just put the start port 1 and end port 65535 on TCP and UDP. ICMP is portless, therefore you need to add only the CIDR address to allow from the whole internet (0.0.0.0/0).
You can also fine tune this in order to allow only one IP, such as 123.123.123.123/32 presuming the ip is 123.123.123.123 or the whole class c, presuming you have IPs in that range (123.123.123.1-123.123.123.254 which translates to 123.123.123.0/24).
Example:
I am running a billing panel on a server some place and wish to allow it to access the solusvm master that i run on a VM in the cloud with Prometeus/Iperweb and deny access to everyone else. Let's suppose the IP where I run the billing panel is 1.2.3.4 and port for solusvm is 5656 (for SSL as it should be used by any sane host) So, I am adding the rule for TCP traffic, port starting at 5656 and ending at 5656 and as CIDR I add the billing panel IP which is 1.2.3.4 and the netmask for only one IP which is 32, so we have:

I strongly advise everyone not to open all ports by default unless they know how to stop all redundant services or not to installt hem at all. Our templates are minimalistic running only port 22 ssh, however, many applications install by default services which are not needed and this increases the risk for 0 days exploits, even if you keep them updated daily. Instead, consult your application documentation and open only the ports needed for it to function. If you know what you are doing, and I suppose most our customers do, go ahead :) Our regular VPSes have all ports open by default, this only eliminates the need for running a firewall in mostt cases, it is not put there to limit you in any way shape or form.
We may offer another security model with all ports open.
Note: IPv6 is still wide open, you will have to use the VMs firewall to filter IPv6 if you choose to enable it and need to offer services over IPv6.
